Are "Russian Hackers" always from Russia?
Nowadays, we can increasingly see press releases after cyberattacks that say that “it was a sophisticated attack, behind which there were statesmen,” which means that the attackers acted in the interests of one or more states. Along with Chinese and North Korean hackers, hackers supporting the Russian government are very often accused of attacks. Of course, we are not here to make blind accusations, so let’s look at a potential example where digital traces lead to Russian hackers.
Incident
It happened, your business has been attacked by crypto-ransomware. During the time-pressured incident response activities, you managed to collect some details: the ransomware note and the IP address from which the compromised account was connected. We’ll take a look at this using the MedusaLocker Ransomware and IP 87.251.70.100 as an example (Important Note: IP was chosen as an example and has never been seen as malicious related)
Pieces of evidence
Let’s take a look at the ransomware note:
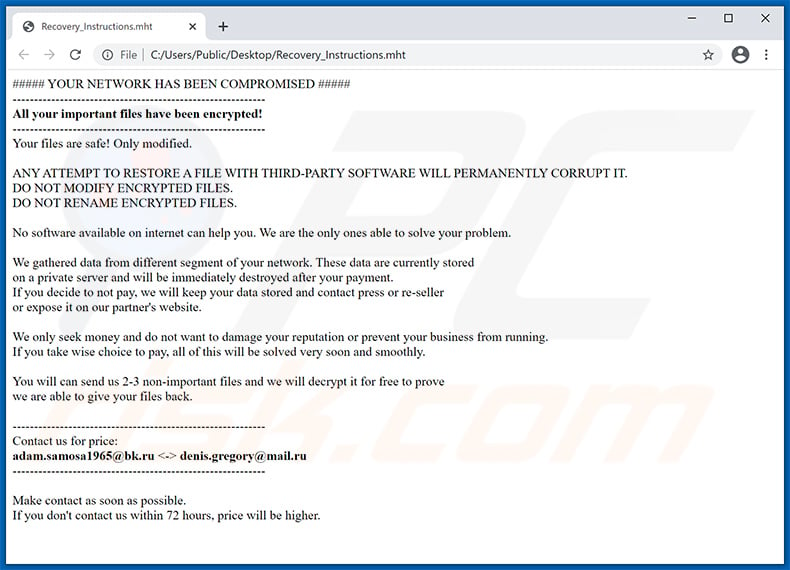
(source of image https://www.pcrisk.com/removal-guides/16693-readinstructions-ransomware )
Contact details contain two email addresses, both under .ru domains, which are definitely associated with the Russian federation.
The second piece is IP – 87.251.70.100. A quick investigation on it with the most common public available tools shows it as Russian Federation located IP.
On the surface, the case is solved and you’ve deduced that Russian hackers targeted your company. The information goes to the next morning press release and is quoted in all news agencies.
Not everything is as it seems
Let’s have a closer look from the perspective of a person who is well versed in Russian culture.
- Email addresses in the ransomware note are in different Russian domains bk.ru and mail.ru, but they belong to the same mail service provider Mail.ru Group. If the threat actor wanted to have two email addresses in case one is promptly shut down because of some abuse/spam report, what is the point of providing them with one email service with different domain names? Moreover, Mail.ru Group is well known in Russia for actively cooperating with law enforcement agencies.
- If the first email address does not make sense from a Russian language perspective, the other provides us with another suspicious clue. Email addresses tend to follow the most common pattern <firstname>.<lastname>, but “denis” and “gregory” are both first names. In Australian culture, it is not uncommon to have a first name as a surname, but in Russia, it is the opposite. There are patronymic names but they have quite specific writing rules and first names are never surnames.
- On the screenshot from Shodan, we can see the organisation as SA Geocentru, which again is uncommon from a Russian language perspective. Without deep-diving into Russian grammatical rules, “Geocentrru” or just “Geocentr” would have been less suspicious. A quick search on ISP “RM Engineering LLC” reveals the organisation site – http://rm-injinering.ru/ is still in “.ru domain” but looking at the contact information reveals an address located in Moldova. Additionally, it was confirmed in the “about us” section.
Based on the facts above, it would seem that a malicious actor(s) only pretended to be Russian related which could only be revealed with deep knowledge of the Russian language and culture. Here we come to the fact that any cultural competence extends the ability to see and understand “hidden” information. It is especially crucial in the cybersecurity field, where malicious actors are speaking in many languages and pretending to be other countries to cover their tracks. This illustrates that every avenue needs to be explored before attribution. Having experts with strong investigative skills and experience, diverse, multi-language darknet intelligence will help your business stay ahead of national threat actors.
Our security assurance team offers qualified OSINT service to help you find your security weaknesses and proactively harden your organisation’s IT infrastructure. Request a free consultation with our team today.
see our
Related resources
Mimecast recently released its State of Email Security Report for 2021. The fifth edition of its annual report used interviews with over twelve hundred of information technology and cybersecurity professionals across the globe to gather vital cybersecurity insights. The report offers an insight into the latest email threats along with advice on how to build cyber resilience and mitigate the risks of email-borne attacks.
Cyber attacks and data breaches have been commonplace in the news headlines for some time now. Although a warning from the media is certainly helpful, there is so much more that can be done when it comes to threat intelligence sharing. Threat intelligence sharing is an important part of the global cybersecurity community effort to tackle cybercrime and should form a part of every organisation’s cybersecurity strategy. Sharing cyber threat intelligence enables organisations to make informed decisions about their cybersecurity, building more effective and robust cyber defences.
One of my favourite annual reports to read is the Verizon Data Breach Investigations Report. It’s packed full of insights about the threat landscape and security leaders, in my opinion, should read this report to get a pulse on what’s happening in cyber-scape.
After all, as cyber leaders, we are here to stop breaches – so the insights gained from real cyber incidents and breaches is gold in learning how to tighten up our defences.
All businesses, large and small, are under increasing pressure to demonstrate that they are managing the risk of cyberattacks. This means having the right processes and controls in place to identify risks and vulnerabilities, protect information, as well as detect, respond, and recover in the event of cybersecurity incidents. As such, many businesses are turning to certification authorities and security frameworks to demonstrate privacy and security best practice and achieve compliance with regulatory bodies. System and Organisation Controls (SOC 2) is one such compliance framework that can help organisations to create a structured approach to cybersecurity.
Frost & Sullivan has recently released its 2021 Frost Radar: Email Security report, where its findings provide a benchmarking framework to help businesses protect their email from cyber threats.
As we operate in an increasingly digital world, every business collect, store, and share more and more data. And, amongst that data is personal information. With the OAIC marking this year’s Privacy Awareness Week (PAW) from Monday 3 May to Sunday 9 May 2021, it’s time for us all to review how we protect our customers’ personal information.
We're Here To Help

